SQL Injection Attacks Becoming More Intense
The mass SQL injection attacks we've mentioned here and here are increasing in number and we're seeing more domains being injected and used to host the attack files. We believe that there is now more than one group using a set of different automated tools to inject the code.
Previously, these attacks have primarily pointed to IP addresses in China and we've seen the following domains being used in addition to the ones we've mentioned previously:
www.wowgm1.cn
www.killwow1.cn
www.wowyeye.cn
vb008.cn
9i5t.cn
computershello.cn
We've now seen other domains being used as well such as direct84.com which is inserted by an SQL injection tool (detected as HackTool:W32/Agent.B) distributed to the Asprox botnet. SecureWorks has a nice write-up available. The direct84.com domain fast-fluxes to several different IPs in Europe, Israel and North America.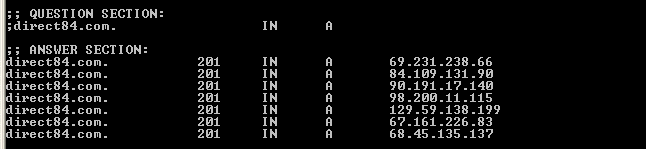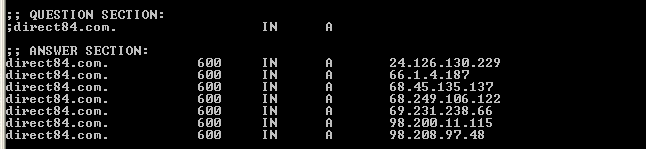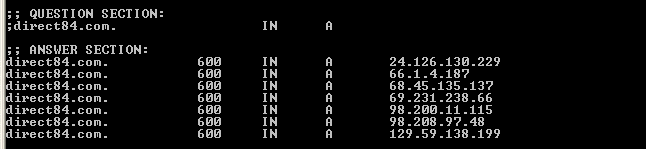
The injected link eventually leads to a backdoor detected as Backdoor:W32/Agent.DAS.
This is a good time to again mention that it's not a vulnerability in Microsoft IIS or Microsoft SQL that is used to make this happen. If you are an administrator of a website that is using ASP/ASP.NET, you should make sure that you sanitize all inputs before you allow it to access the database.
There are many articles on how to do this such as this one. You could also have a look at URLScan which provides an easy way to filter this particular attack based on the length of the QueryString.
[Source: f-secure]



Post a Comment